A elementary style and design principle involves strictly restricting software permissions to information and APIs. apps should not inherently access segregated facts or execute delicate operations.
Confidential instruction. Confidential AI safeguards training information, product architecture, and product weights throughout training from State-of-the-art attackers like rogue directors and insiders. Just defending weights may be crucial in scenarios exactly where model education is source intensive and/or includes sensitive model IP, regardless of whether the teaching data is community.
Confidential Computing may help protect sensitive information used in ML instruction to take care of the privateness of person prompts and AI/ML styles throughout inference and allow secure collaboration in the course of product generation.
Also, we don’t share your details with 3rd-get together model vendors. Your knowledge stays personal for you inside of your AWS accounts.
Seek legal guidance regarding the implications in the output obtained or the use of outputs commercially. ascertain who owns the output from the Scope one generative AI application, and who's liable When the output takes advantage of (for example) non-public or copyrighted information all through inference that is definitely then made use of to produce the output that your organization utilizes.
Pretty much two-thirds (sixty %) of the respondents cited regulatory constraints as a barrier to leveraging AI. A significant conflict for developers that really need to pull all of the geographically distributed facts into a central locale for query and Investigation.
The EUAIA makes use of a pyramid of challenges product to classify workload styles. If a workload has an unacceptable chance (in accordance with the EUAIA), then it'd be banned altogether.
Apple Intelligence is the non-public intelligence program that brings potent generative models to apple iphone, iPad, and Mac. For State-of-the-art features that need to purpose over complicated knowledge with much larger Basis products, we produced personal Cloud Compute (PCC), a groundbreaking cloud intelligence process built specifically for private AI processing.
Confidential AI is a list of hardware-dependent systems that deliver cryptographically verifiable security of knowledge and versions throughout the AI lifecycle, such as when details and products are in use. Confidential AI technologies include accelerators which include common function CPUs and GPUs that guidance the generation of Trusted Execution Environments (TEEs), and expert services that help data selection, pre-processing, coaching and deployment of AI products.
“The validation and protection of AI algorithms employing individual clinical and genomic facts has prolonged been A serious problem during the Health care arena, but it surely’s a person that may be overcome because of the applying of this up coming-technology technological know-how.”
Feeding knowledge-hungry devices pose multiple business and ethical worries. allow me to estimate the top 3:
Please Observe that consent won't be possible in unique circumstances (e.g. You can't gather consent from the fraudster and an employer cannot acquire consent from an worker as There exists a electricity imbalance).
Extensions to the GPU driver to verify GPU attestations, create a protected interaction channel With all the GPU, and transparently encrypt all communications concerning the CPU and GPU
for instance, a fiscal Group could fine-tune an present language design employing proprietary financial info. Confidential safe ai apps AI can be utilized to guard proprietary information as well as the qualified product in the course of high-quality-tuning.
 Tia Carrere Then & Now!
Tia Carrere Then & Now! Bradley Pierce Then & Now!
Bradley Pierce Then & Now!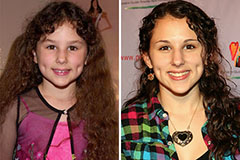 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Michael Oliver Then & Now!
Michael Oliver Then & Now! Barbara Eden Then & Now!
Barbara Eden Then & Now!